NIST Cybersecurity framework is a cybersecurity tool designed to improve and organize your cybersecurity plans. It is a set of strategies and guidelines aimed to assist organizations in their management, reduction, and effective communication against cyber risks for their networks, systems, and assets that store sensitive data. It is a widely used method of determining and addressing high-priority risks that damage your businesses.
The first NIST Framework was released in 2014. Then came an updated version 1.1 in 2018. Since November 6, 2023, the public draft of NIST Cybersecurity Framework 2.0 has been released by NIST for public comments. The final version 2.0 of the NIST Framework is expected to be released in early 2024. Due to the proven versatility of the framework, the agency now encourages organizations and businesses of all sizes to adopt the framework voluntarily.
In this blog, you can find all your queries related to NIST CSF like what it is. What does it comprise and what are the main fundamentals of the framework.
What Is The NIST CyberSecurity Framework?
The NIST Cybersecurity framework is a set of principles and practices formulated by the US National Institute of Standards and Technologies(NIST). The framework applies to businesses of all sizes in their battle against cyber threats. It gives a clear strategy to decide which areas of your cyber security program require more investment and time.
NIST Cyber security framework was primarily designed for government and private organizations. Public companies can also apply the framework to assess the potential threats to their organizations. The U.S. government and NIST provide a useful roadmap to businesses in detecting and reducing the malicious attacks targeted to harm their data
Who Needs NIST CSF ?
NIST Cybersecurity Frameworks are powerful guidelines and tools for any organization that aims to run its business without distortion. It was originally developed for infrastructure sectors but is now celebrated by private companies, research organizations, public companies, and more. Due to comprehensive guidelines, the framework is utilized by 50% of companies for their cybersecurity needs. The framework comprises core components, profiles, and implementation tiers.
Fundamentals Of NIST CSF
The NIST Cybersecurity Framework(CSF) comprises 5 main functions that you can apply to meet all cybersecurity needs. For a better assessment, NIST requires companies to consider their target(combination of threats, objectives, and compliance requirements of the company) before implementing the strategies and guidelines.

1. NIST Framework Profiles
A NIST profile provides you with a roadmap to analyze the current state or main targets of cybersecurity activities. It provides actionable guidance to reduce, manage, and communicate cyber security risks within your organization.
2. Implentation Tiers
By implementing the NIST CSF, organizations can measure their progress into one of these four tiers
a. Tier-1(Partial)
The organization is aware of NIST CSF but lacks processes and plans against effective cybersecurity management
b. Tier-2(Risk Informed)
The organization informally shares cybersecurity risks and awareness. A lack of proper planning and cybersecurity risk management is seen.
c. Tier-3(Repeatable)
The senior executives of the organization are well aware of the cyber threats and devise actionable, organization-wide plans to respond the malicious activities.
d. Tier-3(Adaptive)
The cyber security team continuously evaluates and maps out effective strategies to overcome the detrimental effects of cyber attacks. The organization is cyber-resilient and implements predictive indicators against prevention.
3. Core Functions Of NIST CSF
Organizations can implement NIST CSF in any one of these five areas:
I. Identify
This component includes Business Environment, Risk Assessment, Asset Management, Risk Management Strategy and Governance. It requires the companies and organizations to identify the context of CSF to better prioritize the initiatives that meet their objectives and needs. It gives an organization a complete view of the micro and macro risks posed on the organization’s security.
To identify the existing and upcoming threats, use the following steps :
- List all the equipment, data, and software used including laptops, tablets, smartphones, and point-of-sale devices.
- Share a cybersecurity policy of the company including:
- Roles of vendors, employees, and others having access to sensitive information
- Main steps taken against a cyber attack and preventing the damage it causes
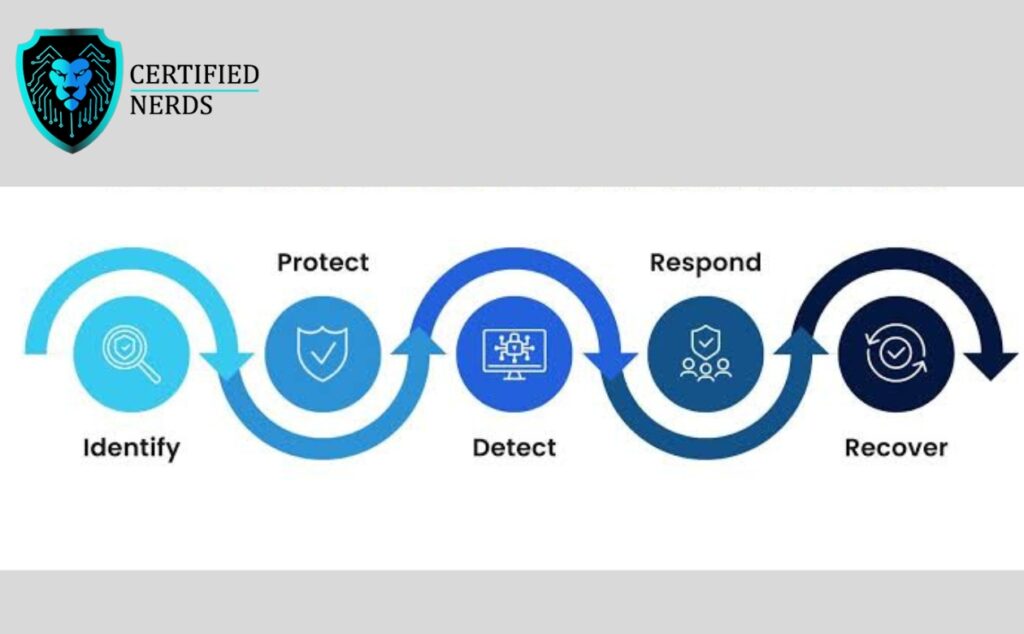
II. Protect
The protection element of NIST CSF creates and implements the strategies and processes that safeguard key systems and sensitive information while alleviating risks and threats. The main categories of the function include:
- Identity Management and Access Control
- Protective Technology
- Awareness and Training
- Data Security
- Information Protection Processes
It also involves establishing procedures and policies that limit the impact of potential threat incidents. For effective protection of your systems, you need to:
- Encrypt data-at-rest and data-in-transit
- Track who uses your computer system and data
- Train employees and others using networks and devices about cybersecurity, its threats, and financial losses
- Automate or update security software regularly
- Have data backups

III. Detect
Continuous security monitoring, anomaly events, and detection processes are the main components of the NIST detection function. A good detection of a cyber attack involves an internal activity of the computer system or identifying negligence of an employee. Timely detection of the upcoming response is the key factor of this function. The sooner your organization detects the hanging threats, the better it becomes prepared to tackle that anomaly.
How to detect potential threats in the computer system?
- Limit the access of unauthorized users, devices, and software to your computer networks.
- Monitor unusual or suspicious activities of users and employees.
IV. Respond
This function ensures documented plans and strategies crafted as an armor against cyber threat incidents. It also involves the upgradation of the security policy of the company as a result of cyber attacks or other preventions learned.
To handle a cyber incident, you need:
- Response Planning
- Mitigation and Improvement
- Communication Analysis(Both external and Internal)
V. Recover
Getting back to normality after a cyberattack incident is a crucial part of the recovery function of NIST. An organized recovery plan takes into account the recovery matrices, operation orders, and objectives. Make sure to keep your customers and employees aware of the best practices and recovery policies while combating a cyber attack.
NIST CSF of recovery phase includes:
- Restoration Policies
- Improvements
- Communications
- Recovery planning
To learn more about the NIST Framework for small businesses, go to the:





